dot - The Deepfake Offensive Toolkit
About the Tool:
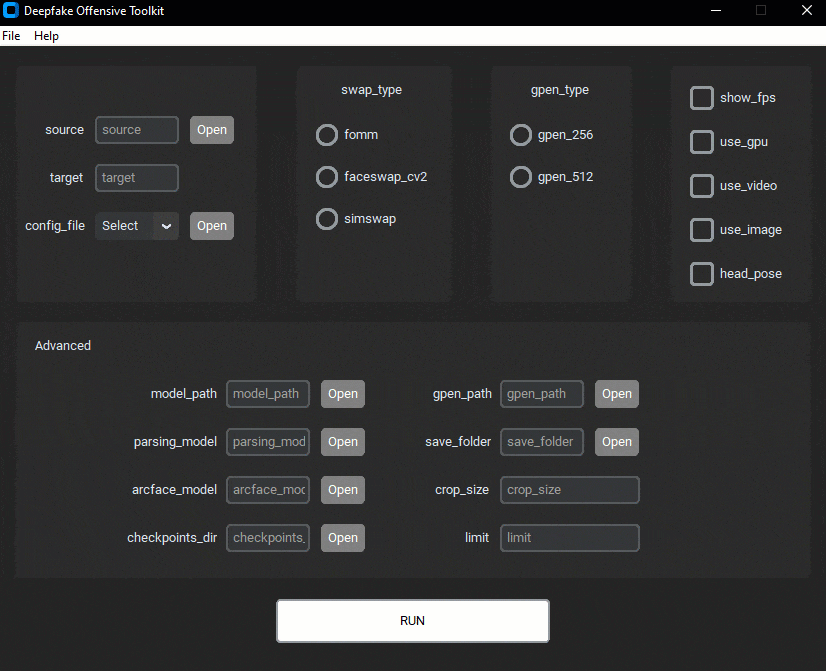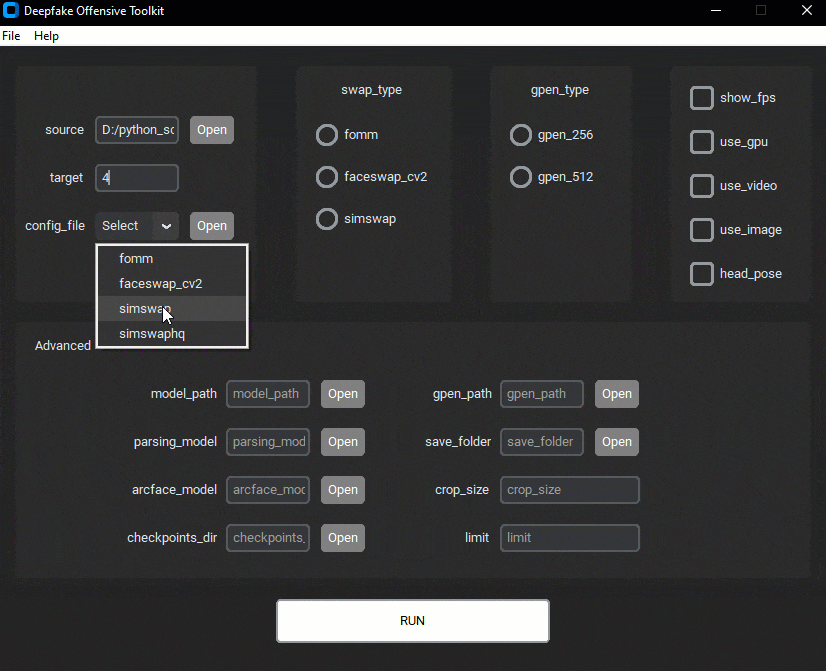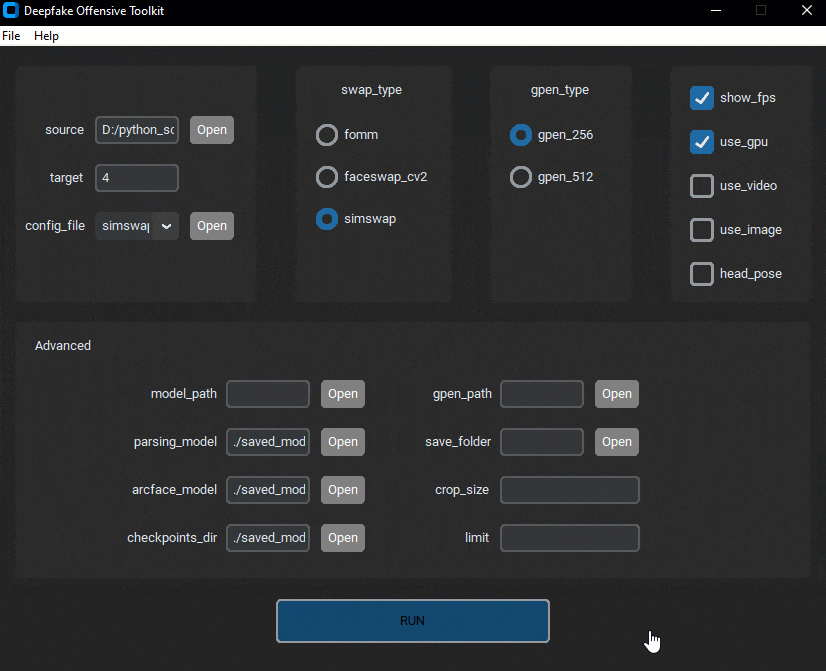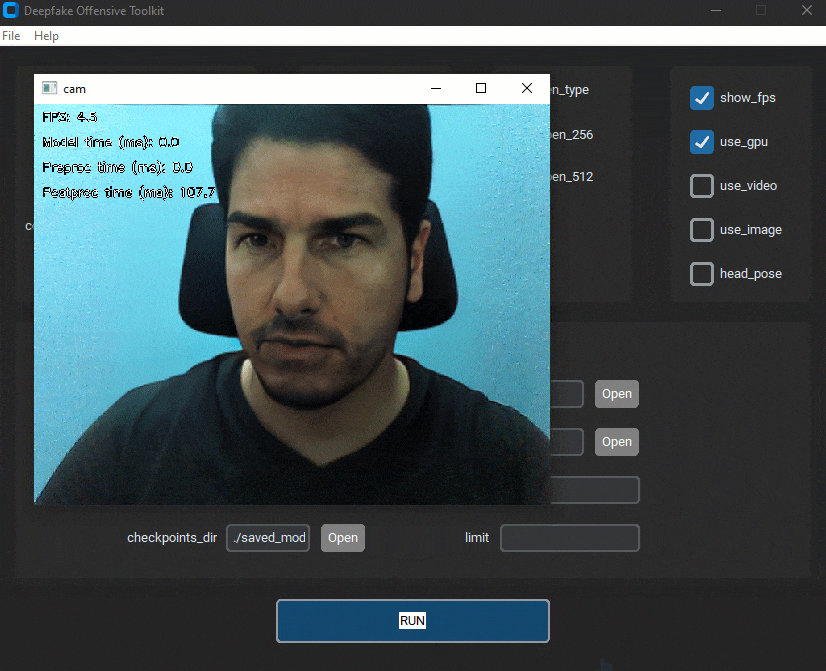
dot (aka Deepfake Offensive Toolkit) makes real-time, controllable deepfakes ready for virtual cameras injection...
- Face Swap
- Lower Quality Face Swap
- FOMM, First Order Motion Model for Image Animation

PyExfil - Exfiltration Techniques
About the Tool:
The purpose of PyExfil is to set as many exfiltration and communication techniques that can be used by various threat actors/malware...
Network Techniques:
- DNS Query
- HTTP Cookie
Communication Techniques:
- NTP Request
- DropBox LSP (Broadcast or Unicast)
Physical Techniques:
- Audio - No listener
- QR Codes
Steganography Techniques:
- Binary Offset
- Video Transcript to Dictionary

WAF Bypass Tool
About the Tool:
WAF Bypass Tool is an open source tool to analyze the security of any WAF for False Positives and False Negatives using predefined and customizable payloads...
Payloads available for: API, GraphQL, LDAP, LFI, NoSQLi, RCE, RFI, SQLi, SSI, SSRF, SSTI, XSS and many more...
Visit GitHub Repository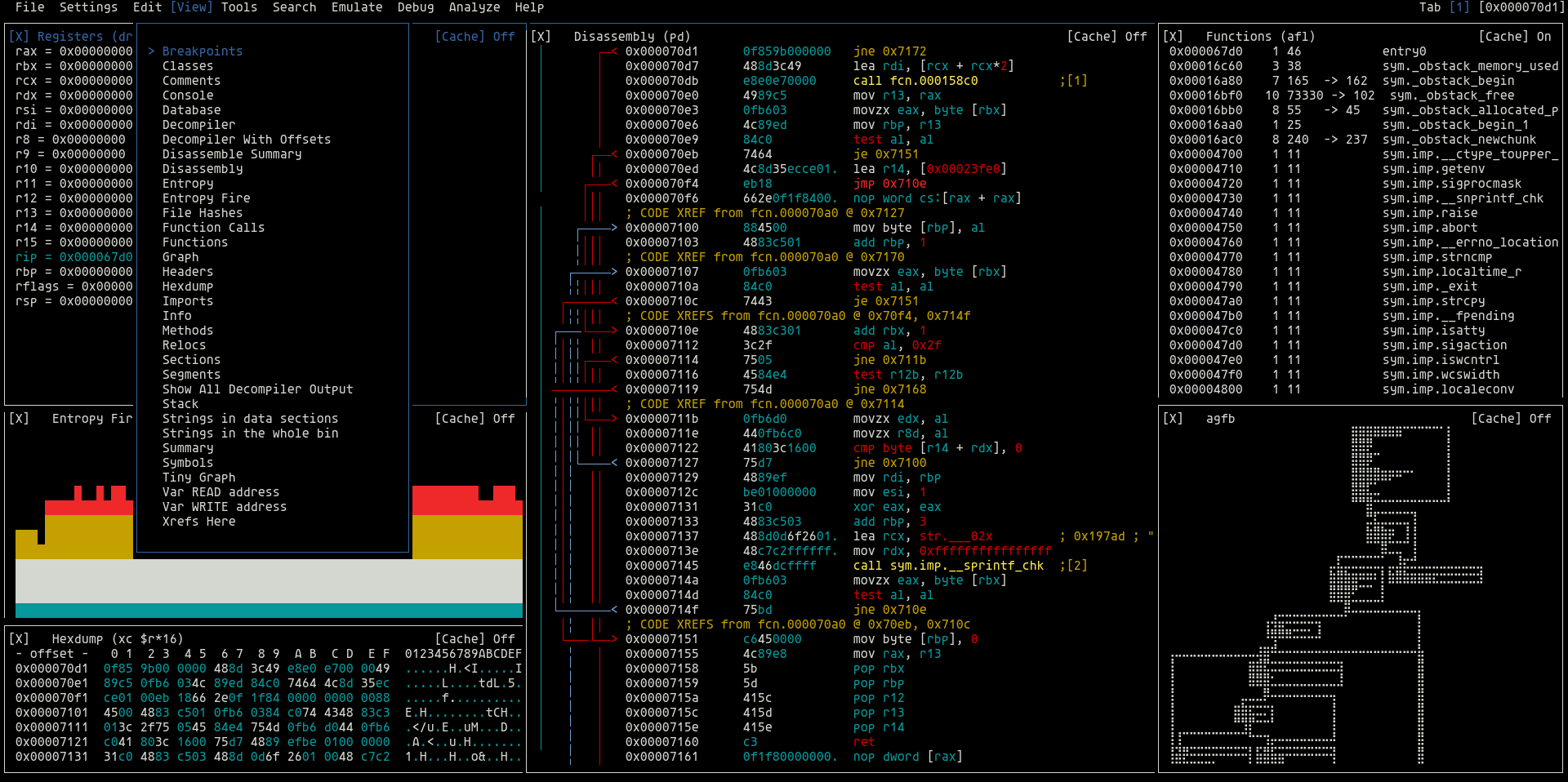
radare2
About the Tool:
radare2 is a complete rewrite of radare. It provides a set of libraries, tools, and plugins to ease reverse engineering tasks...
The radare project started as a simple command-line hexadecimal editor focused on forensics. Today, r2 is a featureful low-level command-line tool with support for scripting...
r2 can edit files on local hard drives, view kernel memory, and debug programs locally or via a remote gdb server. r2's wide architecture support allows you to analyze, emulate, debug, modify, and disassemble any binary.
Visit GitHub Repository
Villain
About the Tool:
Villain is a C2 framework that can handle multiple TCP socket & HoaxShell-based reverse shells, enhance their functionality with additional features...
The framework's main features include:
- Payload generation based on default, customizable, and/or user-defined payload templates (Windows & Linux),
- A dynamically engaged pseudo-shell prompt that can quickly switch between shell sessions,
- File uploads (via HTTP),
- Auto-HTTP request & exec scripts against sessions (a bit unstable),
- Auto-invoke ConPtyShell against a PowerShell r-shell session as a new process to gain a fully interactive Windows shell,
- Team chat,
- Session Defender (a feature that inspects user-issued commands for mistakes / unintentional input that may cause a shell to hang).





0 Comments